[1] C. Munuera, Steganography and error-correcting codes, Signal
Processing 87(6) (2007), 1528-1533.
DOI: https://doi.org/10.1016/j.sigpro.2006.12.008
[2] F. Ayissi Eteme, Logique et Algebre de Structures Mathematique
Modales, Chrysipiennnes Edition Herman, Paris, 2009.
[3] F. Ayissi Eteme and J. A. Tsimi, A modal  approach of the notion of code, Journal of
Discrete Mathematical Science and Cryptography, 14(5) (2001),
445-473.
approach of the notion of code, Journal of
Discrete Mathematical Science and Cryptography, 14(5) (2001),
445-473.
DOI: https://doi.org/10.1080/09720529.2011.10698348
[4] F. Ayissi Eteme and J. A. Tsimi, A 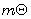 approach of the Algebriac theory of linear
codes, Journal of Discrete Mathematial Sciences and Cryptography 14(6)
(2011), 559-581.
approach of the Algebriac theory of linear
codes, Journal of Discrete Mathematial Sciences and Cryptography 14(6)
(2011), 559-581.
DOI: https://doi.org/10.1080/09720529.2011.10698356
[5] Fidèle Ayissi Eteme and J. A. Tsimi, 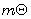 cyclic codes on a
cyclic codes on a 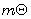 field, International Journal of Mathematics,
Game Theory, and Algebra 25(3) (2016), 313-344.
field, International Journal of Mathematics,
Game Theory, and Algebra 25(3) (2016), 313-344.
[6] F. A. Eteme, Chrysippian 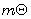 Valent Introducing Pure and Applied
Mathematics, LAP Lambert Academic Pubblishing (2015), Deutschland,
Germany.
Valent Introducing Pure and Applied
Mathematics, LAP Lambert Academic Pubblishing (2015), Deutschland,
Germany.
[7] J. A. Tsimi, A. Kemadjou Kecthandjeu and L. Um, On a class of
modal  convolutional codes, Journal of Information and
Optimization Sciences 42(5) (2021), 995-1026.
convolutional codes, Journal of Information and
Optimization Sciences 42(5) (2021), 995-1026.
DOI: https://doi.org/10.1080/02522667.2020.1835036
[8] J. A. Tsimi, A. Kemadjou Ketchandjeu and L. Um, A 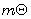 analysis and a decoding
analysis and a decoding 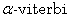 algorithm of the
algorithm of the 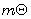 convoulutional codes on
convoulutional codes on  Journal of Information and Optimization
Sciences 42(8) (2021), 1815-1840.
Journal of Information and Optimization
Sciences 42(8) (2021), 1815-1840.
DOI: https://doi.org/10.1080/02522667.2021.1961976
[9] J. A. Tsimi and G. C. Pemha Binyam, On the generalized modal
 Reed-Muller codes, Journal of Information and
Optimization Sciences 42(8) (2021), 1885-1906.
Reed-Muller codes, Journal of Information and
Optimization Sciences 42(8) (2021), 1885-1906.
DOI: https://doi.org/10.1080/02522667.2021.1961977
[10] J. A. Tsimi and R. C. Youdom, The modal  extensions of BCH codes, Journal of Information
and Optimization Sciences, 42(8) (2021), 1723-1764.
extensions of BCH codes, Journal of Information
and Optimization Sciences, 42(8) (2021), 1723-1764.
DOI: https://doi.org/10.1080/02522667.2021.1914364
[11] J. A. Tsimi, R. C. Youdom and B. Boakye, Modal  linear codes with complementary modal
linear codes with complementary modal
 duals, Journal of Information and Optimization
Sciences 42(5) (2021), 1027-1063.
duals, Journal of Information and Optimization
Sciences 42(5) (2021), 1027-1063.
DOI: https://doi.org/10.1080/02522667.2020.1843272
[12] M’hammed Boulagouaz and Mohamed Bouye, Correspondence
between steganographic protocols and error correcting codes, Journal
of Algebra Combinatorics Discrete Structures and Applications 4(2)
(2017), 197-206.
DOI: https://doi.org/10.13069/jacodesmath.284966
[13] Khosravi Sara, Abbasi Dezfoli Mashallah and Yektaie Mohammad
Hossein, A new steganography method based on HIOP (Higher Intensity of
Pixel) algorithm and Strassen’s matrix multiplication, Journal
of Global Research in Computer Science 2(1) (2011), 6-12.
[14] S. Katzenbeisser and F. A. Petitcolas, Information Hiding
Techniques for Steganography and Digital Watermarking, Artech House,
Norwood, MA, 2000.
[15] G. J. Simmons, The prisoners’ problem and the subliminal
channel, in Proc. Advances in Cryptology (CRYPTO ’83), pp.
51-67. Berglund, J. F. and K.H. Hofmann, 1967. Compact semitopological
semigroups and weakly almost periodic functions, Lecture Notes in
Mathematics, No. 42, Springer-Verlag, Berlin-New York.
[16] Christian Cachin, Digital Steganography, Encyclopedia of
Cryptography and Security, 2005.
DOI: https://doi.org/10.1007/0-387-23483-7_115