[1] M. R. K. Ariffin and S. Shehu, New attacks on prime power RSA
modulus 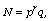 Asian Journal of Mathematics and Computer
Research (2016), 77-90.
Asian Journal of Mathematics and Computer
Research (2016), 77-90.
[2] M. A. Asbullah and M. R. K. Ariffin, New attacks on RSA with
modulus 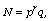 using continued fractions, Journal of Physics,
Conference Series, Volume 622, No. 1, IOP Publishing, 2015.
using continued fractions, Journal of Physics,
Conference Series, Volume 622, No. 1, IOP Publishing, 2015.
[3] D. Boneh, G. Durfee and N. Howgrave-Graham, Factoring 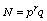 for large r, Advances in Cryptology
CRYPTO’99, Lecture Notes in Computer Science 1592 (1999),
326-337.
for large r, Advances in Cryptology
CRYPTO’99, Lecture Notes in Computer Science 1592 (1999),
326-337.
[4] J. Blomer and A. May, A generalized Wiener attack on RSA, In
Public Key Cryptography - PKC 2004, Lecture Notes in Computer Science
2947 (2004), 1-13.
[5] A. Fujioka, T. Okamoto and S. Miyaguchi, ESIGN: An efficient
digital signature implementation for smart cards, Advances in
Cryptology EURO-CRYPT 91, Springer-Verlag (1991), 446-457.
[6] G. H. Hardy and E. M. Wright, An Introduction to the Theory of
Numbers, Oxford University Press, London, 1975.
[7] J. Hinek, On the Security of Some Variants of RSA, PhD. Thesis,
Waterloo, Ontario, Canada, 2007.
[8] N. Howgrave-Graham and J. P. Seifert, Extending wieners attack in
the presence of many decrypting exponents, In Secure Networking-CQRE
(Secure)’99, 1740 (1999), 153-166.
[9] A. K. Lenstra, H. W. Lenstra and L. Lovasz, Factoring polynomials
with rational coefficients, Mathematische Annalen 261 (1982),
513-534.
[10] A. May, New RSA Vulnerabilities Using Lattice Reduction Methods,
PhD. Thesis, University of Paderborn, 2003.
[11] A. Nitaj, Diophantine and lattice cryptanalysis of the RSA
cryptosystem, Artificial Intelligence, Evolutionary Computing and
Metaheuristics, Springer Berlin, Heidelberg (2013), 139-168.
[12] A. Nitaj, Cryptanalysis of RSA using the ratio of the primes,
Progress in Cryptology-AFRICACRYPT 2009, Springer Berlin, Heidelberg
(2009), 98-115.
[13] A. Nitaj, M. R. K. Ariffin, D. I. Nassr and H. M. Bahig, New
attacks on the RSA cryptosystem, Progress in Cryptology-AFRICACRYPT
2014, Springer International Publishing (2014), 178-198.
[14] A. Nitaj, A New Vulnerable Class of Exponents in RSA, 2011.
[15] T. Okamoto and S. Uchiyama, A new public-key cryptosystem as
secure as factoring, Advances in Cryptology-EUROCRYPT’98,
Springer-Verlag (1998), 308-318.
[16] R. Rivest, A. Shamir and L. Adleman, A method for obtaining
digital signatures and public-key cryptosystems, Communications of the
ACM 21(2) (1978), 120-126.
[17] S. Sarkar, Small secret exponent attack on RSA variant with
modulus 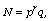 designs, Codes and Cryptography 73(2) (2014),
383-392.
designs, Codes and Cryptography 73(2) (2014),
383-392.
[18] T. Takagi, Fast RSA-type cryptosystem modulo 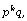 In Advances in Cryptology-Crypto’98,
Springer (1998), 318-326.
In Advances in Cryptology-Crypto’98,
Springer (1998), 318-326.
[19] M. Wiener, Cryptanalysis of short RSA secret exponents, IEEE
Transactions on Information Theory 36 (1990), 553-558.