[1] F. Ayissi Eteme, 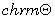 Introducing Pure and Applied Mathematics,
Lambert Academic Publishing Saarbruken, Germany, 2015.
Introducing Pure and Applied Mathematics,
Lambert Academic Publishing Saarbruken, Germany, 2015.
[2] J. A. Tsimi and Rose C. Youdom, The modal  extensions of BCH codes, Journal of Information
and Optimization Sciences 42(8) (2021), 1723-1764.
extensions of BCH codes, Journal of Information
and Optimization Sciences 42(8) (2021), 1723-1764.
DOI: https://doi.org/10.1080/02522667.2021.1914364
[3] J. A. Tsimi and Pemha B. G. Cedric, A 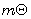 spectrum of Reed-Muller codes, Journal of
Discrete Mathematical Sciences and Cryptography 25(6) (2022),
1791-1807.
spectrum of Reed-Muller codes, Journal of
Discrete Mathematical Sciences and Cryptography 25(6) (2022),
1791-1807.
DOI: https://doi.org/10.1080/09720529.2020.1814489
[4] F. A. P. Petitcolas, R. J. Anderson and M. G. Kuhn, Information
hiding: A survey, Proceedings of the IEEE 87(7) (1999), 1062-1078.
DOI: https://doi.org/10.1109/5.771065
[5] F. A. Eteme and J. A. Tsimi, A 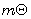 approach of the algebraic theory of linear
codes, Journal of Discrete Mathematical Sciences and Cryptography
14(6) (2011), 559-581.
approach of the algebraic theory of linear
codes, Journal of Discrete Mathematical Sciences and Cryptography
14(6) (2011), 559-581.
DOI: https://doi.org/10.1080/09720529.2011.10698356
[6] W. Bender, W. Butera, D. Gruhl, R. Hwang, F. J. Paiz and S.
Pogreb, Applications for data hiding, IBM Systems Journal 39(3-4)
(2000), 547-568.
DOI: https://doi.org/10.1147/sj.393.0547
[7] F. Ayissi Eteme, Logique et Algèbre de Structure Mathématiques
Modales 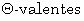 Chrysippiennes, Edition Hermann, Paris,
2009.
Chrysippiennes, Edition Hermann, Paris,
2009.
[8] F. Ayissi Eteme, Complétion chrysippienne d’une algèbre de
Lukasiewicz 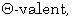 CRAS Paris, 299, Série 1(3) (1984), pp.
69-72.
CRAS Paris, 299, Série 1(3) (1984), pp.
69-72.
[9] R. Crandall, Some Notes on Steganography, 1998.
[10] A. Westfeld, F5–A Steganographic Algorithm: High Capacity
Despite Better Steganalysis, in: Lecture Notes in Computer Science,
Volume 2137, Springer, New York, 2001, pp. 289-302.
DOI: https://doi.org/10.1007/3-540-45496-9_21
[11] F. A. Eteme and J. A. Tsimi, A modal 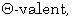 approach of the notion of code, Journal of
Discrete Mathematical Sciences and Cryptography 14(5) (2011),
445-473.
approach of the notion of code, Journal of
Discrete Mathematical Sciences and Cryptography 14(5) (2011),
445-473.
DOI: https://doi.org/10.1080/09720529.2011.10698348
[12] J. A. Tsimi and Pemha B. G. Cedric, On a decoding algorithm of
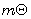 Reed-Muller codes, Journal of Discrete
Mathematical Sciences and Cryptography, 2021.
Reed-Muller codes, Journal of Discrete
Mathematical Sciences and Cryptography, 2021.
DOI: https://doi.org/10.1080/09720529.2021.1920189
[13] J. A. Tsimi and Pemha B. G. Cedric, On the generalized modal
 Reed-Muller codes, Journal of Information and
Optimization Sciences 42(8) (2021), 1885-1906.
Reed-Muller codes, Journal of Information and
Optimization Sciences 42(8) (2021), 1885-1906.
DOI: https://doi.org/10.1080/02522667.2021.1961977
[14] F. Ayissi Eteme, Anneau chrysippien 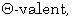 CRAS, Paris 298, Série 1 (1984), pp.1-4.
CRAS, Paris 298, Série 1 (1984), pp.1-4.