[1] E. Biham and A. Shamir, Differential Cryptanalysis of DES-like
Cryptosystems, Lect. Notes Comp. Sci. Springer, 537 (1990), 2-21.
[2] E. Biham and A. Shamir, Differential cryptanalysis of the full
16-round DES, Differential cryptanalysis of the Data Encryption
Standard, pp. 79-88. Springer, New York.
[3] C. Carlet, P. Charpin and V. Zinoviev, Codes, bent functions and
permutations suitable for DES-like cryptosystems, Designs, Codes and
Cryptography 15(2) (1998), 125-156.
DOI: https://doi.org/10.1023/A:1008344232130
[4] D. Coppersmith, The Data Encryption Standard and its strength
against attacks, IBM Journal of Research and Development 38(3) (1994),
243-250.
DOI: https://doi.org/10.1147/rd.383.0243
[5] C. Blondeau and K. Nyberg, Perfect nonlinear functions and
cryptography, Finite Fields and Their Applications 32 (2015),
120-147.
DOI: https://doi.org/10.1016/j.ffa.2014.10.007
[6] C. Bracken, E. Byrne, N. Markin and G. McGuire, New families of
quadratic almost perfect nonlinear trinomials and multinomials, Finite
Fields and Their Applications 14(3) (2008) 703-714.
DOI: https://doi.org/10.1016/j.ffa.2007.11.002
[7] M. Brinkman and G. Leander, On the classification of APN functions
up to dimension five, International Workshop on Coding and
Cryptography (WCC), Versailles, France, 2007.
[8] K. A. Browning, J. F. Dillon, M. T. McQuistan and A. J. Wolfe, An
APN permutation in dimension six, Finite Fields: Theory and
Applications 518 (2010), 33-42.
[9] L. Budaghyan, C. Carlet, P. Felke and G. Leander, An infinite
class of quadratic APN functions which are not equivalent to power
mappings, Proceedings of ISIT 2006, Seattle, USA, 2006.
[10] L. Budaghyan, C. Carlet and G. Leander, Another class of
quadratic APN binomials over 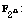 the case n divisible by 4, Proceedings
of the Workshop on Coding and Cryptography (WCC07) (2007), 49-58.
the case n divisible by 4, Proceedings
of the Workshop on Coding and Cryptography (WCC07) (2007), 49-58.
[11] L. Budaghyan, C. Carlet and G. Leander, Constructing new APN
functions from known ones, Finite Fields and Their Applications 15(2)
(2009), 150-159.
DOI: https://doi.org/10.1016/j.ffa.2008.10.001
[12] C. Carlet, Vectorial Boolean functions for cryptography, Boolean
Models and Methods in Mathematics, Computer Science and Engineering
134 (2010), 398-469.
[13] H. Dobbertin, Almost perfect nonlinear power functions on
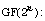 The Welch case, IEEE Transact. Inform. Th.
45(4) (1999), 1271-1275.
The Welch case, IEEE Transact. Inform. Th.
45(4) (1999), 1271-1275.
DOI: https://doi.org/10.1109/18.761283
[14] H. Dobbertin, Almost perfect nonlinear power functions on
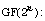 The Niho case, Information and Computation
151(1-2) (1999), 57-72.
The Niho case, Information and Computation
151(1-2) (1999), 57-72.
DOI: https://doi.org/10.1006/inco.1998.2764
[15] H. Dobbertin, Almost perfect nonlinear power functions on
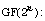 A new case for n divisible by 5, In: D.
Jungnickel and H. Niederreiter, Editors; Proceedings of the Conference
on Finite Fields and Applications, Augsburg 1999, Springer-Verlag,
Berlin (2001), 113-121.
A new case for n divisible by 5, In: D.
Jungnickel and H. Niederreiter, Editors; Proceedings of the Conference
on Finite Fields and Applications, Augsburg 1999, Springer-Verlag,
Berlin (2001), 113-121.
[16] Y. Edel, G. Kyureghyan and A. Pott, A new APN function which is
not equivalent to a power mapping, IEEE Trans. Inform. Th. 52(2)
(2006), 744-747.
DOI: https://doi.org/10.1109/TIT.2005.862128
[17] R. Gold, Maximal recursive sequences with 3-valued recursive
cross-correlation functions, IEEE Trans. Inform. Th. 14(1) (1968),
154-156.
DOI: https://doi.org/10.1109/TIT.1968.1054106
[18] F. Gologlu, APN Trinomials and Hexanomials, arXiv: 1411.2981v1,
(2014).
[19] H. Janwa, G. McGuire and R. M. Wilson, Double-error-correcting
cyclic codes and absolutely irreducible polynomials over GF(2),
Journal of Algebra 178(2) (1995), 665-676.
DOI: https://doi.org/10.1006/jabr.1995.1372
[20] H. Janwa and M. Wilson, Hyperplane sections of Fermat varieties
in 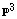 in chapter 2 and some applications to cyclic
codes, Applied Algebra, Algebraic Algorithms and Error-Correcting
Codes, Proceedings AAECC-10 (G. Cohen, T. Mora and O. Moreno Editors),
Lecture Notes in Computer Science, Springer-Verlag, New York/Berlin
673 (1993), 180-194.
in chapter 2 and some applications to cyclic
codes, Applied Algebra, Algebraic Algorithms and Error-Correcting
Codes, Proceedings AAECC-10 (G. Cohen, T. Mora and O. Moreno Editors),
Lecture Notes in Computer Science, Springer-Verlag, New York/Berlin
673 (1993), 180-194.
[21] T. Kasami, The weight enumerators for several classes of subcodes
of the second order binary Reed-Muller codes, Information and Control
18(4) (1971), 369-394.
DOI: https://doi.org/10.1016/S0019-9958(71)90473-6
[22] X. Lai, J. L. Massey and S. Murphy, Markov ciphers and
differential cryptanalysis, Advances in Cryptology-Eurocrypt’91,
Lecture Notes in Computer Science, Springer-Verlag 547 (1991),
17-38.
[23] K. Nyberg and L. R. Knudsen, Provable Security Against
Differential Cryptanalysis, Proceedings of the 12th Annual
International Cryptology Conference on Advances in Cryptology,
Springer-Verlag (1992), 566-574.
[24] K. Nyberg and L. R. Knudsen, Provable security against a
differential attack, Journal of Cryptology 8(1) (1995), 27-37.
DOI: https://doi.org/10.1007/BF00204800
[25] K. Nyberg, Differentially uniform mappings for cryptography,
Advances in Cryptology-Eurocrypt’93, Springer-Verlag (1994),
55-64.
[26] F. Rodier, Bornes sur le degre des polynomes presque parfaitement
non-lineaires, Contemporary Math., AMS, Providence (RI) USA 487
(2009), 169-181.
[27] W. Stallings, Cryptography and Network Security Principles and
Practice, Fifth Edition, New York, Pearson, 2010.